Solaris, FreeBSD, NetBSD, OpenBSD, Mac OS X and Windows. Wireless Hacking. A tool for Windows that facilitates detection of.
DNS enumeration is the process of locating all the DNS servers and their corresponding records for an organization. A company may have both internal and external DNS servers that can yield information such as usernames, computer names, and IP addresses of potential target systems.
NSlookup, DNSstuff, the American Registry for Internet Numbers (ARIN), and Whois can all be used to gain information that can then be used to perform DNS enumeration.
NSlookup and DNSstuff
One powerful tool you should be familiar with is NSlookup (see Figure 1). This tool queries DNS servers for record information. It's included in Unix, Linux, and Windows operating systems. Hacking tools such as Sam Spade also include NSlookup tools.
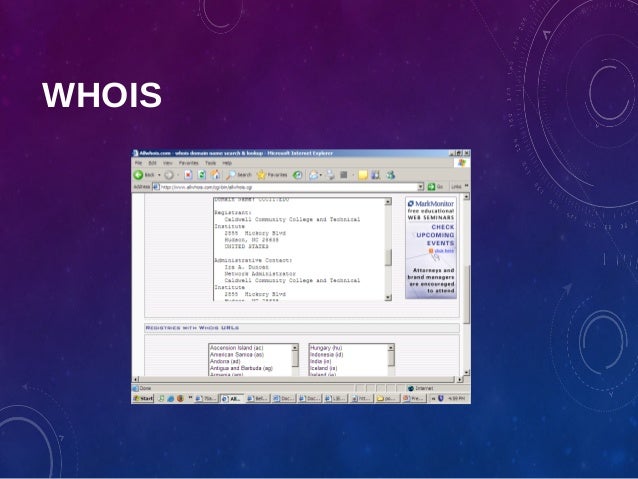
Building on the information gathered from Whois, you can use NSlookup to find additional IP addresses for servers and other hosts. Using the authoritative name server information from Whois (AUTH1.NS.NYI.NET), you can discover the IP address of the mail server.
The explosion of easy-to-use tools has made hacking easy, if you know which tools to use. DNSstuff is another of those tools. Instead of using the command-line NSlookup tool with its cumbersome switches to gather DNS record information, just access the website www.dnsstuff.com, and you can do a DNS record search online. Figure 2 shows a sample DNS record search on www.eccouncil.org using DNSstuff.com.
This search reveals all the alias records for www.eccouncil.org and the IP address of the web server. You can even discover all the name servers and associated IP addresses.
This is a selection of footprinting and scanning tools you may wish to install in your MIS Lab machine in order to do the course assignments. You should be very careful in using these tools outside of the Lab. Network administrators do not take lightly the probing of their networks and may respond aggressively to your attempts to gain information about them by using some of these tools. Please note that I am emphasizing Windows tools, but we will see Linux/UNIX tools later.Sam Spade Hacking Tool
CyberKit
Start by downloading CyberKit from this Web site and install it. CyberKit is a graphical tool and will let you do the following:- whois (under WhoIs), as shown in class.
- single ping (under Ping) and ping sweep (under NetScanner, ping addresses).
- traceroute (under TraceRoute), as shown in class.
- port scanning (under NetScanner, ScanPorts as shown here.
Sam Spade
Download Sam Spade from this web site and install it. Sam Spade is also a graphical tool which allows you to do DNS interrogation and many other things. The features which make Sam Spade a key security tool are:- Advanced DNS - DIG tool requests all the DNS records for a host or domain
- Zone Transfer - ask a DNS server for all it knows about a domain
- SMTP Relay Check - check whether a mail server allows third party relaying
- Scan Addresses - scan a range of IP addresses looking for open ports
- Crawl Web site - search a Web site, looking for email addresses, offsite links, download a Web site
- Search IP block - finds the IP block for an organization
Pinger
Download Pinger from its ftp location and install it. Pinger is a very fast ping sweeper as shown in class. Once you obtain the IP block of the target organization, you use pinger to see what hosts are active.SuperScan
Download SuperScan from its new location and install it. SuperScan allows you to scan a range of IP addresses and do TCP port scanning. It can check all ports, or the ones you select. It is a very fast and powerful tool. Once you obtain the active hosts using Pinger you can cut in the time SuperScan will find which ones have active ports.WUPS
Download WUPS from its Web site and install it. WUPS allows you to check UDP ports, to complement your study of hosts with active ports (TCP plus UDP). WUPS can only do one host at a time, but you can also select what ports to look for. You can see here a list of TCP and UDP ports, but be aware that hackers have been using some unnamed ports for Trojans, backdoors, etc.Active Ports
Active Ports is a free tool for Windows NT/2000/XP that enables you to monitor all open TCP and UDP ports on the local computer. You can download it from the Smartline free download site. As you can see in this image it shows not only the open ports, but also what application in your PC is linked to the open ports. If a connection is established with a remote host you can see the remote host IP number. Active Ports is not a Intrusion Detection System, but provides a picture of is going on in your computer regarding to ports.